SentinelOne creates decoy files that have read/write access to help with ransomware detection. SentinelOne will periodically recreate these files if deleted.


The new Vulnerability Insight and Threat Alerts (VITA) Team will be the home of documentation, discussion, and tooling for Information Security Services (ISS)-supported vulnerability management and endpoint detection & response solutions (presently Qualys and SentinelOne, respectively). This Team will act as a hub for campus IT practitioners to receive news about these tools and a forum to direct relevant questions to ISS. The associated SharePoint site will include documentation on deploying and using these tools. To gain access to the VITA team, please contact mailto:soc@uwaterloo.ca.
The new Vulnerability Insight and Threat Alerts (VITA) Team will be the home of documentation, discussion, and tooling for Information Security Services (ISS)-supported vulnerability management and endpoint detection & response solutions (presently Qualys and SentinelOne, respectively). This Team will act as a hub for campus IT practitioners to receive news about these tools and a forum to direct relevant questions to ISS. The associated SharePoint site will include documentation on deploying and using these tools. To gain access to the VITA team, please contact mailto:soc@uwaterloo.ca.
University of Waterloo owned, managed PCs receive SentinelOne (S1) Endpoint Detection and Response (EDR).
|
Non-managed, University-owned PCs should still install SentinelOne. To do so, please first consult with your local IT rep, who may escalate the request to IST.
For personal machines, please review the list of recommended alternatives.
SentinelOne creates decoy files that have read/write access to help with ransomware detection. SentinelOne will periodically recreate these files if deleted.   |
It is not good practise to run multiple EDR/antivirus-type agents. They may “discover” each other and attempt to remove the other or start to mitigate a threat and then be unable to complete the task as the other has gotten there first. SentinelOne is centrally managed and monitored and is the best solution for University-owned equipment. |
By design, endpoint detection and response software is necessarily invasive. It monitors running processes, the network connections they make, files they open, etc. |
This would need to be a discussion with Information Security Services (ISS) as some agreements may require some form of EDR, while others may restrict administrative access to the systems, and so on. Every situation will be different. |
In general, the agent will notify the user.
If you believe SentinelOne is interfering with a legitimate process, submit an inquiry via Jira Help Portal with the device name and affected process and/or file information. If you believe SentinelOne is interfering with a legitimate process, submit an inquiry via Jira Help Portal with the device name and affected process and/or file information. 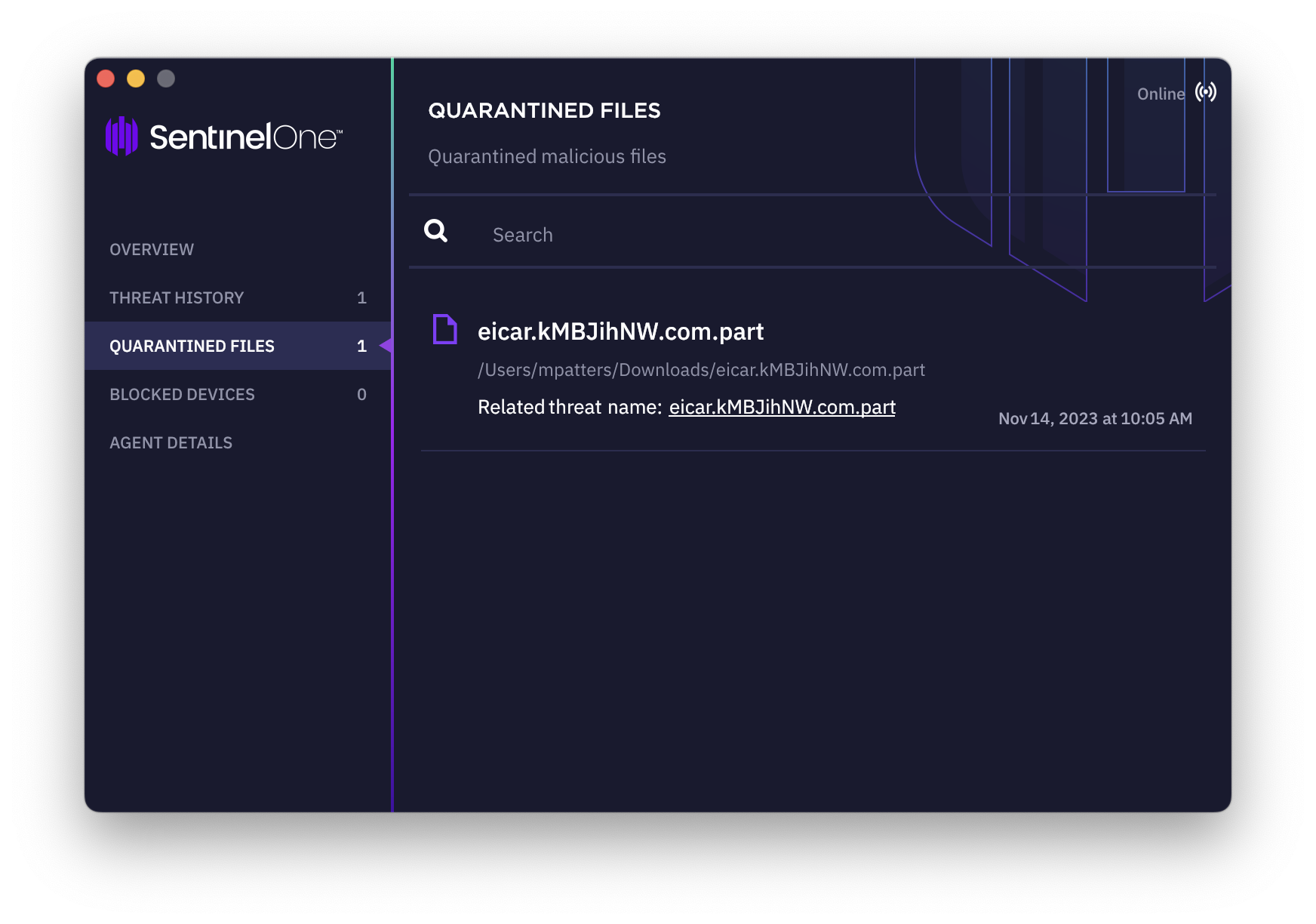 |
Access to the complete set of information collected is restricted to Security Operations staff. While operational log retention varies, SentinelOne data is not kept for longer than a year. Some selected information may be made available to local IT staff members who have need to see logging information. |
S1 is licensed for University-owned equipment. While historically, Waterloo has made use of generous site licenses from other vendors, such licenses are no longer available at a reasonable cost. |
The University does not use S1 to watch an individual’s personal use of the University networks or devices. The University will not use this data to support investigations related to employee productivity, attendance/activity and any other general monitoring of behaviour not directly associated with security threat protection at the University. |
Designated Information Security Services staff will interact with the data only if a security threat alert has been triggered. SentinelOne (S1) uses artificial intelligence to analyze basic file data such as file name, size, and file hashes to find potentially malicious files. Still, it does not analyze content data beyond threat detection. This is consistent with best practices to mitigate against constantly evolving cyber threats. |
The group involved in the request for proposal (RFP) included representatives from multiple faculty IT units as well as IST staff from Information Security Services and Client Services. |
SentinelOne monitors computer and network activity for behaviour that is consistent with cybersecurity threats. Devices are registered with SentinelOne using identifiers related to the device itself, not the individual(s) using the device. Information is only stored when a threat is detected, and an alert is generated. Personal information would only be stored when incidental to a cybersecurity alert. The collection and storage of any information related to an alert, including personal information, is vital to understand the impact of a potential breach, and necessary to comply with the University’s breach disclosure obligations (statutory and contractual). |
Information Security Services (ISS) will be developing tooling to provide IT personnel with access to reports on systems for which they are responsible. Unfortunately, direct access to the console by non-administrators is extremely difficult to manage in a distributed environment such as Waterloo’s, and can create difficulties in correctly managing endpoints, groups, and exceptions. |
While both are security-oriented applications, they perform different functions. Qualys VMDR collects information about installed software and operating system configuration and reports on vulnerabilities. This is a relatively passive process that makes no changes to the system. S1 examines processes as they run, and the files they open, and attempts to determine if these processes are behaving maliciously. It can respond by terminating processes or quarantining files. This is an active process that can make changes to the computer. And while S1 has vulnerability management functionality, and Qualys has EDR functionality, neither was designed originally to fulfil the other function, and so we have chosen best-of-breed software in both cases. |
While we obviously do not currently have a great deal of experience with S1, it did support macOS 14 “Sonoma” upon release, and does not include documentation, for example, that requires Linux kernel versions to be pinned. We are reasonably confident that S1 will not cause blocks for new versions of Windows, Linux distributions, or macOS |
While there are never any guarantees, IST staff did successfully upgrade Debian and macOS systems with S1 installed. |
S1 may be disabled and is un-installable but requires active confirmation from an EDR administrator. This is because in the past, malware that did slip past endpoint protection software would immediately disable or uninstall that protection. In other words, this is to maintain the integrity of the software installation and to ensure continued protection of the computer and, by extension, Waterloo information resources and infrastructure. |
S1 has been run at Waterloo on 7000 systems for five months (as of November 2023) and there have been only a few (three) logged complaints. Most users do not notice a slowdown. The biggest issue has been with full disk scans on older hardware. S1 does run regular full disk scans, but they are not often – every 3-4 weeks, and it does attempt to throttle disk usage during regular hours. If you suspect or know that S1 is causing a deleterious effect for an unacceptable length of time, please work with your local IT support and IST to determine the cause. |
Service catalogue feedbackIf you’d like to share any feedback about this service catalogue entry, please let us know. |